Table of Contents
Cybersecurity loves its fancy words, and you’re in for a treat! ASM, DRPs, EASM, CAASM, let’s dive into the depths of Attack Surface Management.
In this article, you will learn about:
- what Attack Surface Management is;
- the 3 main areas of an attack surface;
- the major concepts, tools and technologies of ASM;
- the 5 key steps of any sound ASM strategy;
- and how offensive security can complement it.
Attack Surface Management is a critical component of cybersecurity risk management, as it helps organizations proactively identify weaknesses and remediate them before they can be exploited. It’s becoming increasingly important as organizations’ attack surface grows, i.e. through cloud computing. As a matter of fact, Gartner even ranked attack surface expansion as the top trend for security and risk management in 2022.

What is Attack Surface Management (ASM)?
Attack Surface Management (ASM) is a process of identifying, analyzing, and managing the various points of entry that cybercriminals could exploit to gain unauthorized access to an organization’s network or assets. It involves mapping out all the possible ways that an attacker could penetrate an organization’s defenses, such as software vulnerabilities, network configurations, third-party integrations, and other potential weak points.
ASM must always look at things from an attacker’s perspective, with a red team mindset rather than a blue team one. The idea is quite simple: think like an attacker to identify entry points and vulnerabilities that could be exploited to reach your target.
The 3 areas of an Attack Surface
It is commonly accepted that an organization’s attack surface consists of three main areas:
- Physical Attack Surface such as premises, which are vulnerable to on-site intrusions.
- Social Engineering Attack Surface. It’s basically about people, who can be targeted by social engineering attacks, blackmail, etc.
- Digital Attack Surface, which is anything that can be targeted by a cyber attack.
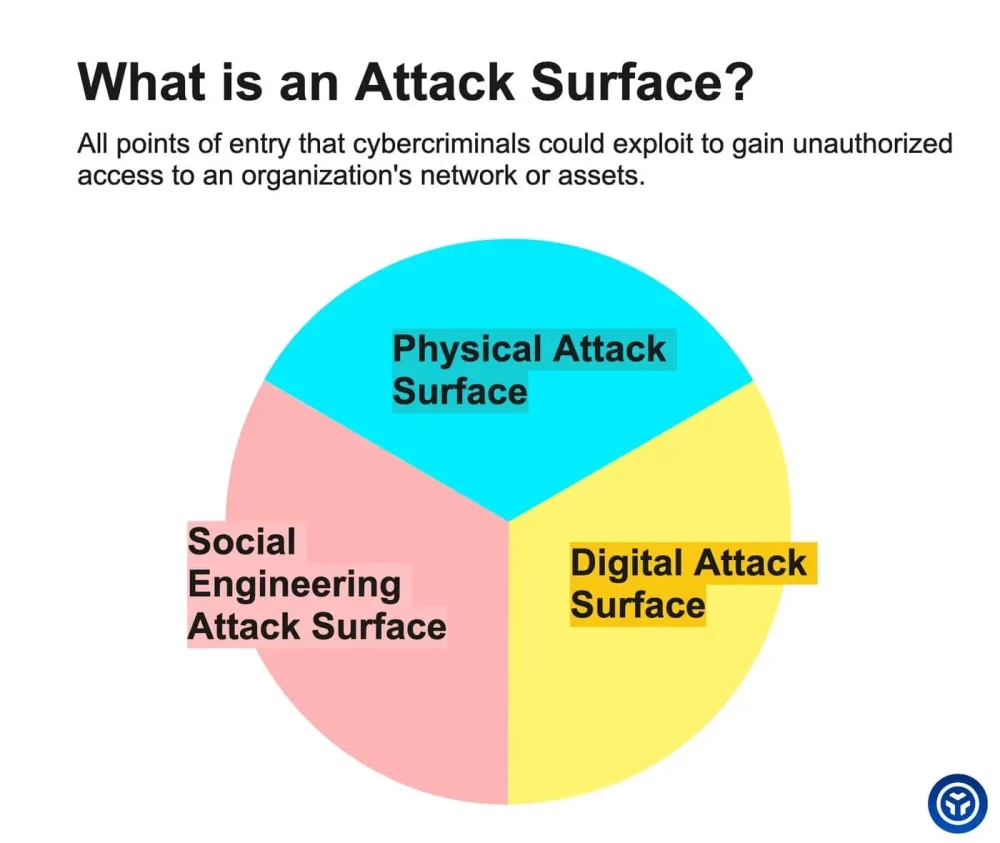
Since this blog is mainly about digital security, this is the part of the Attack Surface we will focus on. But keep in mind that Attack Surface Management isn’t just about cybersecurity and digital attack surface.
The 5 steps of an Attack Surface Management strategy
An Attack Surface Management strategy should consists of (at least) those 5 core steps:
- Asset Discovery: know your assets and exposure;
- Analysis: analyze them for potential risks and CVEs;
- Prioritization: decide what needs to be addressed first;
- Remediation: get the job done;
- Monitoring – and repeat.
As you can see, ASM is broad and involves several activities, including vulnerability scanning, penetration testing, red teaming, configuration management, threat modeling, and continuous monitoring. It requires a multidisciplinary approach involving IT professionals, security experts and risk management teams.
Attack Surface Management tools and technologies
Regarding IT-related assets, Attack Surface Management can be broken down into 3 main technologies:
- Digital Risk Protection services (DRPs)
- Cyber Asset Attack Surface Management (CAASM)
- External Attack Surface Management (EASM)
What are Digital Risk Protection Services?
DRPs are vendors offering Digital Risk Protection managed services. They aim to protect brand and reputation by identifying and mitigating digital risks across social media and all parts of the web (Clear, Dark and Deep Web). It’s more about ensuring that companies aren’t exposed to threats, such as impersonation or leakage of sensitive information, than it is about looking for vulnerabilities within the attack surface.
DRPs address digital footprint and threat monitoring, while CAASM and EASM focus on asset-based security risks – even though some vendors embrace several roles simultaneously. Recently, the term Exposure Management has been coined to go beyond Vulnerability Management, and thus encompass everything that isn’t related to CVEs.
What is Cyber Asset Attack Surface Management (CAASM)?
Cyber Asset Attack Surface Management (CAASM) tools provide security teams with greater asset awareness and visibility. They offer a comprehensive view of the organization’s internal and external assets.
CAASM solutions most often work through API integrations with other products and data sources, and add to the existing tech stack. This means that, while they can prove useful, they don’t provide extensive asset discovery nor vulnerability assessment. In a nutshell, CAASM should be seen as a detailed mapping of existing and known assets (internal and external) rather than anything else. Here’s a list of CAASM vendors by Gartner.
What is External Attack Surface Management (EASM)?
External Attack Surface Management (EASM) is a specific type of attack surface management that focuses on the points of entry that are accessible from the internet. That means websites, web applications, APIs, remote access points, cloud services and more.
The word EASM is often used to refer to cybersecurity solutions that address this particular aspect of attack surface management. As you might guess, EASM tools focus on Internet-facing assets. Here’s a list of EASM vendors by Gartner.
Unlike CAASM, EASM solutions are designed for asset discovery. These detections will feed the CAASM process, which is more about having a big picture than reconnaissance.
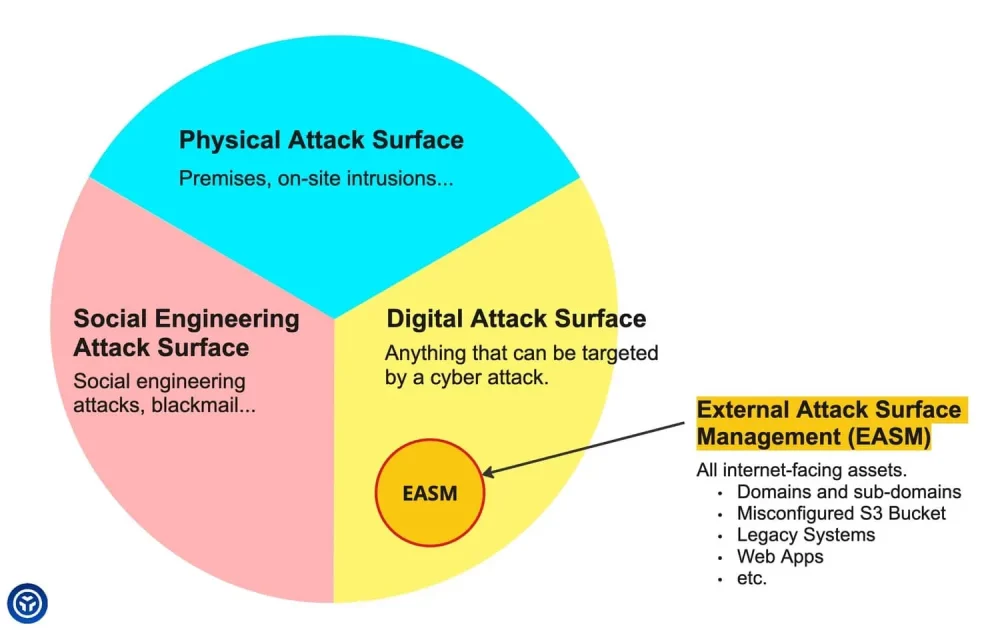
Although, EASM is not just about recon. Attack Surface Discovery is obviously an important part of External Attack Surface Management, but you have to actually manage your findings – it’s in the name, isn’t it?
The discovery phase must be followed by identifying and prioritizing the risks associated with each asset all the way to remediation of vulnerabilities, and everything in between. This means scanning and manually testing assets, prioritizing remediation efforts on newly found vulnerabilities, and ideally doing so on a regular or ongoing basis.
Truth is, your sec team is probably already doing EASM
EASM may sound like yet another cool kid thing to implement, but it is actually what many security teams have been doing for a long time.
EASM tools can prove useful as an added layer of automation, but the EASM mindset and practices have been around for a while. Red teamers didn’t wait for EASM as a tool to dive into asset discovery and vulnerability testing.
For many organizations, EASM is not so much about adding tasks and workflows, but rather organizing and documenting them under a new program. If anything, it should reduce the workload by streamlining what is already in place.
Automation is not enough
Any security expert will agree that vulnerability scanners alone are not enough to test the cybersecurity of an asset. And just as scans aren’t enough to find all CVEs, EASM tools aren’t enough to find all assets exposed on the Internet.
Automation on its own is not sufficient, and leveraging human expertise is key:
- in asset discovery
- and security testing of those points of entry.
This is where Offensive Security comes in, as it serves both.
Offensive security as part of an Attack Surface Management strategy
We said it right from the start, but we will repeat it because it is crucial: Attack Surface Management must be carried out with an attacker’s mindset. And that’s why Offensive Security is so effective when it comes to ASM. It comes in many forms, such as Pentest as a Service, but it is bug bounty that best complements EASM strategies.
Bug bounty contributes to asset discovery and analysis, which as a reminder are the first two steps of an Attack Surface Management strategy – 1) Asset discovery ; 2) Analysis ; 3) Prioritization ; 4) Remediation ; 5) Monitoring.
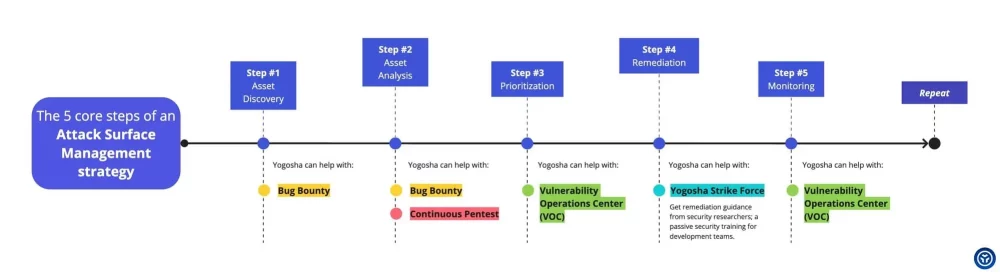
Step 1: Bug bounty for Asset Discovery
The idea behind bug bounty is quite simple. An organization calls on ethical hackers to test its assets; real attackers who try to find vulnerabilities. If they find a vulnerability, they receive a bounty. If the hackers find nothing, the company spends nothing.
All right, but what does this have to do with asset discovery, you ask?
The thing is, security researchers are incredibly resourceful when it comes to unearthing the most vulnerable assets, and often to the surprise of the targeted organization. This is confirmed by Antonin Garcia, the CISO of Veepee, whose e-commerce platform records 4.5 million unique visitors and 130K€ of orders per day.
“We know how to do pentesting, and the applications that are very exposed for members, we know them. But bug bounty allows you to go after the blind spots, the small services that are not necessarily maintained or with less rigor.” – Antonin Garcia, Veepee’s CISO
A statement backed up by Julien Reitzel, Lead Offensive Security at Veepee: “Thanks to Yogosha, we already learned about a number of perimeters, subdomains and servers exposed on the Internet that we hadn’t had a chance to look at before. It allowed us to cut off things that we weren’t necessarily aware of.”
Step 2: OffSec for Asset Analysis
As you can imagine, hackers don’t find assets just for sport. Then comes the analysis stage of your ASM strategy, aka security testing.
Security researchers are particularly effective because they think outside the box. A scanner is useful to find the most known CVEs, the low-hanging fruits so to speak. Hackers can find the most critical vulnerabilities, that require time and ingenuity. Vulnerabilities that truly matter, the ones you don’t want to miss.
Here again, Veepee’s CISO confirms the value of bug bounty:
“We’ve done a lot of pentests, we always do some for compliance or to get back on critical applications. […] But with bug bounty, it’s different. You’re not waiting for a report, you’re waiting for a critical vulnerability. That’s the difference as well. And with Yogosha, criticals have almost always been relevant. It’s not the secure cookie or the poorly configured HSTS that you can get from a pentester that gets to the end of its 5 days, and has to make a report despite not having found much.” – Antonin Garcia, Veepee’s CISO

E-Book: Bug bounty, the ultimate guide to a successful program
Learn how to build your Bug Bounty program, make it attractive and leverage hackers to identify high-risk vulnerabilities.
Step 3: Prioritization through CVSS
Vulnerabilities uncovered by security testing must be prioritized in order to direct remediation efforts. Fortunately, those identified through offensive security testing can be quickly assessed through the Common Vulnerability Scoring System (CVSS) – at least if you’re using our platform.
Each vulnerability report you receive is assigned a score, which allows you to assess its criticality at a glance. You can then forward it to the team in charge of remediation (that’s Step 4 of the ASM Strategy), via any of our integrations or API.
Step 4: Remediation guidance from security researchers
When it comes to remediation, there’s no secret: your technical teams need to fix the issue. But they don’t have to do it all alone.
Security researchers from the Yogosha Strike Force can provide remediation guidance for the vulnerabilities they have discovered. Your teams can interact with hackers directly via our platform and inquire about the next steps. If a vulnerability report raises questions about how to fix it, just ask and the hacker will surely be able to point you in the right direction.
In other words, hackers provide passive training for development teams, who can learn from them. A side benefit of bug bounty observed by the CISO of Teréga, a major player in gas transport and storage in Europe.
“Yogosha’s researchers have a certain ethic, and they share their experience with development teams. With bug bounty, we improve the know-how and sensitivity of in-house developers. It’s a continuous training effect.” – Philippe Puyou Lascassies, CISO at Teréga

Step 5: Monitoring through Analytics Dashboards
This brings us to the 5th and final step of the Attack Surface Management strategy: monitoring. Our Vulnerability Operations Center allows CISOs and security teams to centralize all their assets in one tool, even across multiple entities. Monitoring and analytics dashboards then provide a holistic view of the security of your organization – evolution of detections, most vulnerable endpoints, trends in the types of CVEs discovered, etc.
Why is Continuous Attack Surface Management (CASM) important?
Attack Surface Management is not something you do once and then forget about. New vulnerabilities may appear, new assets may be deployed without you knowing it. After all, what security team hasn’t experienced the joys of Shadow IT, i.e. dev and product teams going rogue and pushing things on their own.
Attack Surface Management is something that needs to be done over and over again, and ideally on an ongoing basis. And as always, the cybersecurity scene didn’t miss the opportunity to invent a convoluted acronym: CASM, for Continuous Attack Surface Management.
In short, CASM is about taking the 5 steps of your Attack Surface Management strategy, and repeating them continuously. Ideally by using automated detections like EASM tools, and human expertise through offensive security (whether led by an internal redteam or a cybersecurity specialist like us).
Offensive Security as part of CASM
A bug bounty program can be temporary, but is most effective when continuous. A bug bounty conducted 24/7 on a front-end site or a very sensitive exposure ensures a permanent security monitoring, with hackers scratching at it all year long. And if you give them carte blanche on a domain and allow them to be inventive, you’ll be surprised at the assets they can unearth.
Continuous pentesting is also an optimal approach for an ongoing asset analysis. It’s basically like a traditional pentest, except that it’s not conducted solely over a few days or weeks but all year long. And if you happen to be interested in our services, know that we make sure to mobilize different researchers within the Yogosha Strike Force throughout the year, in order to maintain a continuous watch while diversifying ideas and approaches.
To sum up
- Attack Surface Management (ASM) is the process of identifying, analyzing, and managing the various entry points of an organization’s attack surface. It must always be performed from an attacker’s point of view;
- An organization’s attack surface consists of 3 main areas: Physical, Social and Digital;
- An Attack Surface Management strategy should consist of at least 5 core steps: Asset discovery, Analysis, Prioritization, Remediation and Monitoring;
- ASM encompasses several approaches and technologies, such as DRPs, CAASM and EASM;
- Digital Risk Protection services (DRPs) help to protect brand and reputation by mitigating digital risks across social media and all parts of the web (Clear, Dark and Deep Web);
- CAASM solutions help security teams map their organization’s existing and known assets, but do not provide in-depth asset discovery or vulnerability assessment;
- External Attack Surface Management (EASM) is a specific type of attack surface management that focuses on the points of entry that are accessible from the internet. The automation approach of EASM solutions is necessary, but not sufficient to address all the threats;
- Offensive Security strengthens some steps of a good ASM strategy, namely Asset Discovery and Asset Analysis;
- Bug bounty and continuous pentesting contribute to a CASM approach – Continuous Attack Surface Management –, which is another fancy acronym for saying that Attack Surface Management should never end!
Need assistance in analyzing your assets as part of an Attack Surface Management strategy?





