Table of Contents
What are the practical differences between conventional pentesting and Penetration Testing as a Service (PtaaS)? Let’s take a closer look, point-by-point.
Penetration tests are commonplace in offensive security, and their efficiency is no longer to be proven. But this doesn’t mean they can’t be improved. Traditional pentesting is showing its limits in the face of diversifying threats, both in terms of flexibility and strike force.

Crowdsourced cybersecurity offers a new perspective: Penetration Testing as a Service, or PtaaS. The idea is simple: the pentest is not conducted by a consulting firm or a usual service provider, but by a platform that mobilizes its community of researchers and ethical hackers. The difference may seem trivial, and yet…
Pentest as a Service and the traditional approach differ in many ways, from the time to launch to the price, the communication with the pentesters or the reporting rhythm.
Let’s take a look at these two different approaches to the same exercise.
1. How long to launch a pentest?
Traditional Pentest
Before launching a pentest, one must first define its scope as well as the vulnerabilities to be excluded from the searches – brute force attacks for example. As part of a traditional pentest, this step generally involves meetings, phone calls and emails between the organization and the service provider. It’s also at this stage that the price and duration of the pentest are decided. Most often, the penetration test begins 3 to 6 weeks after all these questions have been answered.
Pentest as a Service
The “as a service” approach makes it possible to launch a pentest in a few days, or even in less than 24 hours if all stakeholders move fast. On our side, we have noticed that the launch of a Pentest as a Service generally occurs in less than a week from the first contact. Note that with a PtaaS, the operation can be extended on the fly if the initial duration turns out to be insufficient.
2. Who conducts the pentest ?
Traditional Pentest
The penetration test is performed by a professional pentester, who usually works for an IT consulting firm. Most penetration tests are conducted by one to two in-house pentesters. Most of the time, the client company has no control over the pentester(s) chosen for the mission.
Read also: Penetration testing: why and how to conduct a pentest
Pentest as a Service
With the collaborative approach, the penetration test is performed by researchers operating via a platform. These researchers are usually ethical hackers or professional pentesters working in addition to their main job. The number of researchers allocated to a crowdsourced pentest is theoretically limited only by its budget.

By leveraging the security researcher community, PtaaS can multiply skills on the fly. After all, each researcher has his or her own unique talents. The organization can thus choose the profiles best suited to its budget and scope, depending on the ecosystem targeted – web, cloud, API, etc. – technologies involved or suspected vulnerabilities.
The expertise of researchers can vary significantly from one platform to another. Some public platforms open their doors to everyone with a simple registration, beginners as well as seasoned experts. Others have adopted a private and selective community model, like the Yogosha Strike Force.
3. The remuneration of the pentester/ethical hacker
Traditional Pentest
The pentester is usually an employee of the firm commissioned to perform the pentest. He therefore receives a salary at the end of the month, regardless of the number of audits conducted.
Pentest as a Service
It is hard to say for each platform, as the remuneration models can vary from one to another. At Yogosha, hunters are paid at an average daily rate for pentest operations.
4. What about the communication with the pentesters ?
Traditional Pentest
As part of a classic penetration test, communication with pentesters can vary from one firm to another. Most of the time, internal teams will have little or no interactions with them. The majority of exchanges are done via a single point of contact, a project manager for example.
Pentest as a Service
Using a platform, communication between internal teams and researchers is direct and regular throughout the project. This close collaboration offers three significant advantages over the conventional approach:
- Direct exchanges with researchers make the pentest process more streamlined by removing superfluous middlemen;
- Points of friction or misunderstanding can be discussed, clarified and resolved during the pentest to make it more efficient;
- The company’s employees can increase their skills by working alongside ethical hackers.
5. When are the pentest results available ?
Traditional Pentest
This is one of the main flaws of “old-fashioned” penetration tests, since the results are often communicated at the end of the mission. Potentially critical vulnerabilities are therefore not addressed for several days, or even several weeks. At the end of the pentest, the consulting firm usually provides a report in the form of an encrypted PDF. It lists the vulnerabilities identified by level of criticality, and can suggest ways of remediation.
Pentest as a Service
The company is alerted via the platform as soon as a hacker finds a vulnerability. Vulnerabilities are reported as they are discovered, and internal teams can tackle their corrections even though the pentest is not finished. Even better, a patch can be deployed and immediately tested against hackers without having to run another penetration test.
In addition, this continuous reporting system combined with the possibility of exchanging with ethical hackers makes it easier for internal teams to learn about the remediation of certain vulnerabilities. A service that can be charged extra during a traditional pentest.

E-Book: Bug bounty, the ultimate guide to a successful program
Learn how to build your Bug Bounty program, make it attractive and leverage hackers to identify high-risk vulnerabilities.
Pentester syndrome and Proof Of Concept
Unfortunately, it is not uncommon for a pentest report to deliberately exaggerate the criticality of certain vulnerabilities. This phenomenon is so recurrent that it has a name: the “Pentester Syndrome”.
Some vulnerabilities are presented as being important when they are, most of the time, trivial in terms of security. These include the classic HSTS headers, TLS and SSL protocol issues, and DMARC, DKIM and SPF configurations. The intention is to make the report more relevant than it really is by blowing smoke in the face of the customer. In addition to its lack of honesty, this practice is detrimental to the security of organizations since it distorts the information needed to properly prioritize vulnerabilities and corrective actions.
To avoid this kind of inconvenience, it is better to ask for a Proof Of Concept (POC) when a vulnerability seems exaggerated. A proof of concept is a technical demonstration that proves that the vulnerability is really exploitable, and that it therefore presents a real threat to the security of the asset in question.
As part of a Pentest as a Service with Yogosha, each vulnerability identified by one of our hunters must be accompanied by a POC.
6. Double checking
Traditional Pentest
Here again, it all depends on the chosen provider. But in most cases, traditional providers do not include the verification of corrections by their pentesters. If this service exists, it can be invoiced extra.
Pentest as a Service
Again, it depends on the platform selected. Regarding the tests conducted with Yogosha, the double-check by hunters is included and is not a charged option.
7. How does the pentest integrate with the company’s tools and ecosystems ?
Traditional Pentest
The answer could not be simpler : a traditional pentest does not integrate into the work environments of internal teams. Exchanges take place by phone calls or emails, and reports are communicated through similar channels. It is then up to the internal teams to integrate the results of the pentest into the company’s workflows.
Pentest as a Service
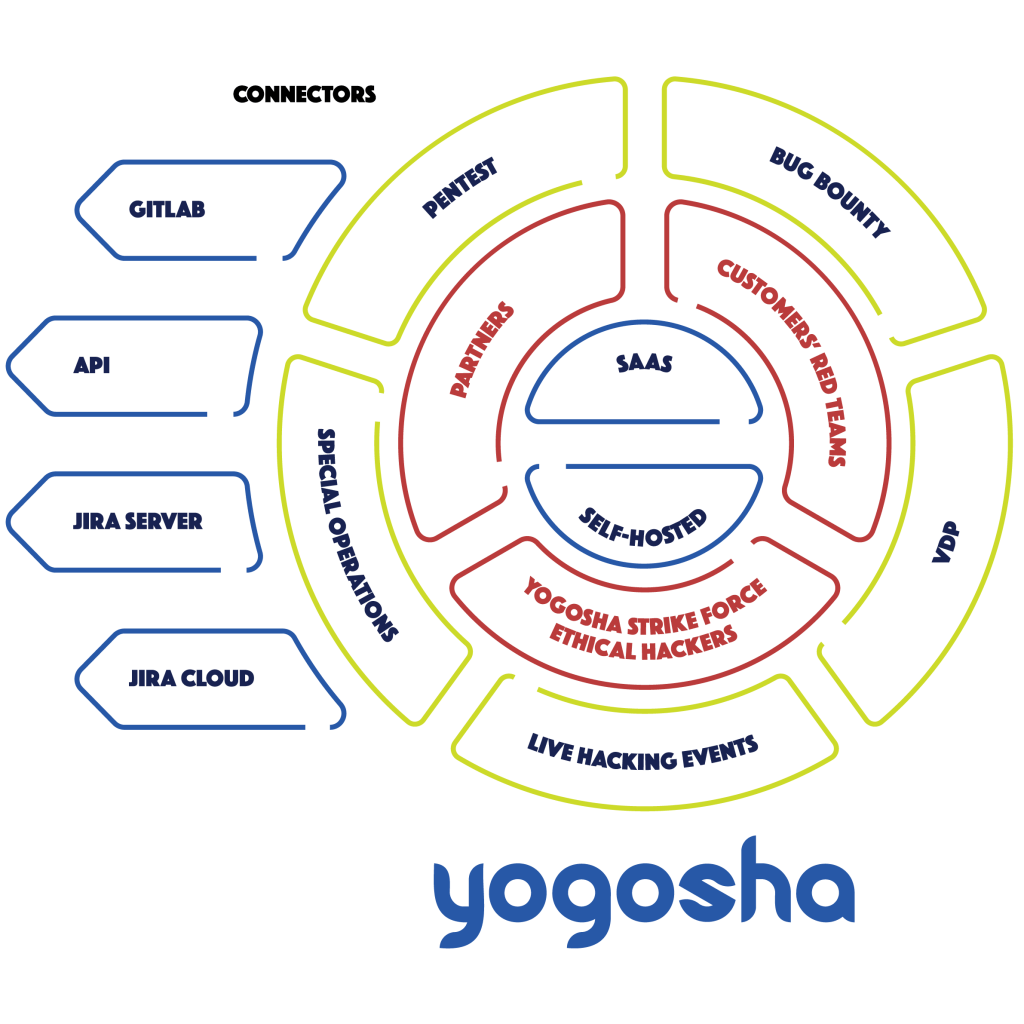
By going through a platform, the pentest integrates with the organization’s tools and ecosystems – for Yogosha, via API, Gitlab, Jira Cloud and Jira Server.
Vulnerability reports can be exported on the fly, and the most critical vulnerabilities can be sent directly to remediation teams. The workflow is much smoother, and vulnerability management much more efficient.
8. What about vulnerability management ?
Traditional Pentest
The most classic penetration tests are completely unrelated to vulnerability management. Vulnerability management may be subject to another contract with an IT consulting firm, but it is completely independent of the penetration testing activity.
Pentest as a Service
Going through a crowdsourced security platform ensures access to the various features it offers. Including those dedicated to vulnerability management.
With Yogosha, reports are centralized in our Vulnerability Operations Center. Teams only have to use one tool, and reports are processed directly from the platform. Assets are organized in different workspaces, with advanced user and rights management, audit logs, SSO authentication, different wallets, analytical dashboards, etc. In short, a true end-to-end vulnerability management solution.
9. What is the cost of a pentest?
Traditional Pentest
The price of a penetration test can range from 4K€ to 150K€ or more. The differences are such that it is impossible to give a standard pricing, both for the traditional approach and for the PtaaS. The price naturally depends on the nature of the pentest – scope, duration, number of pentesters, required skills, etc.
Pentest as a Service
Financially, PtaaS is – in general – more interesting than the traditional approach. The rates are globally more attractive for companies, but it is mostly the removal of many hidden costs that makes the difference.
Since we are not the most objective on the subject, we refer you instead to this article by Tech Beacon: 4 hidden costs of pentesting. It states that the ROI for Pentest as a Service can be up to 96% higher than its historical counterpart.
Penetration Testing as a Service, a more agile and efficient approach
If the PtaaS is much more effective than its traditional counterpart, it is ultimately for two fairly simple reasons.
- Firstly, the digitization of pentesting through a platform allows unparalleled flexibility and responsiveness;
- Second, the collaborative approach relies on the community of ethical hackers. This strength in numbers guarantees unprecedented efficiency and adaptability.

Pentest as a Service (PtaaS) benefits in a nutshell
- A launch in less than a week against 3 to 6 weeks for a traditional pentest;
- Calling on the ethical hacker community allows for the diversification of profiles and skills according to the specificities of the scope;
- Transparent and continuous communication with hackers makes the pentest much more agile and efficient;
- There is no need to wait for the end of the penetration test to receive a report. Vulnerabilities are reported as soon as they are discovered, and remediation of the most critical ones can be done without delay;
- A PtaaS integrates perfectly with organizations’ tools, environments and workflows;
- The company’s internal teams can develop their skills through contact with security researchers;
- Platforms ensure the proper digital transformation of the pentesting activity – which can be of a real interest for MSSPs and such;
- They allow a legal and contractual framework for collaborative pentest, whether in the relationship with hackers or in terms of compliance;
- The Vulnerability Operations Center (VOC) makes it possible to simplify and centralize vulnerability management before, during and after the pentest.
Looking for a modern approach to pentesting? Explore Penetration Testing as a Service with Yogosha, or contact us!