Table of Contents
Some entities regulated by DORA are required to carry out enhanced security tests, in the form of Threat-Led Penetration Testing (TLPT). Here’s how it works.
Nota Bene: This article is the third chapter of our guide to security testing for DORA-regulated entities, which we recommend you read from the beginning if you haven’t already.
In the previous chapters, we discussed digital operational resilience testing, the “classic” tests that all entities within the scope of DORA are required to perform annually. But some organizations are subject to an additional testing obligation: “Threat-Led Penetration Tests”, or TLPTs.
This article will be based primarily on two documents, which will be mentioned several times:
- The official text of DORA (Source), published in December 2022, and more specifically Articles 26 and 27, which address the subject of TLPTs;
- The draft Regulatory Technical Standards (RTS) specifying elements related to Threat-Led Penetration Testing (Source), published at the end of November 2023 by the European Supervisory Authorities (ESAs). Indeed, DORA entrusts them with the responsibility of establishing the technical standards for carrying out a TLPT, and this document is the first version to be made public. This text will be submitted to the European Commission on July 17, 2024, and is therefore not definitive. However, it’s a safe bet that the differences between this draft and the final version will be minimal, so we believe it’s wise to use it.
You can continue reading this chapter published as an article on our blog, or download the full DORA-guide to security testing below in PDF format for easier reading.

DORA: A Guide to Security Testing for Regulated Entities
A 60-page compliance guide to walk security managers of DORA-regulated entities through the regulation's security testing obligations: the resilience testing program, and Threat-Led Penetration Testing (TLPT).
What Is a Threat-Led Penetration Test (TLPT)?
Threat-Led Penetration Tests (TLPT) are enhanced security tests reserved for financial entities whose failure would have systemic effects, and which are most likely to be targeted by malicious actors. For anyone wishing to maximize their profits or destabilize a part of the financial system, a major international bank is obviously more appealing than a relatively modest management company.
As you will see later, TLPTs are carried out under the supervision of the authorities. They are therefore a mechanism for verifying the actual resilience of the financial entities that are essential to the functioning of our financial system.
Resilience tests are intended to raise the level of security of regulated entities, while TLPTs aim to verify that the job has been done by the book, and that the security of the entities is effective.

In Practical Terms, What Does This Mean?
Admittedly, as it stands, the formula “threat-led penetration testing” is impressive, but somewhat cryptic. Let’s start with DORA’s official definition:
‘Threat-led penetration testing (TLPT)’ means a framework that mimics the tactics, techniques and procedures of real life threat actors perceived as posing a genuine cyber threat, that delivers a controlled, bespoke, intelligence-led (red team) test of the financial entity’s critical live production systems. – DORA, Article 3(17)
A TLPT is therefore a large-scale Red Team exercise — and not a mere pentest — which must simulate all the elements of a real attack, and test the entire attack surface of regulated entities. It is commonly accepted that an organization’s attack surface is composed of three main areas:
- The physical attack surface, such as premises, which are vulnerable to on-site intrusions;
- The human attack surface, which relates to people, who can be targeted by social engineering attacks, blackmail, etc.
- The digital attack surface, i.e. everything that can be targeted by a cyber attack.
To be valid and effective, a TLPT must test each of these elements. The Red Team must therefore carry out assaults against information systems in production, social engineering attacks (phishing, baiting, watering hole, etc.), physical intrusion attempts into premises, and much more. In a proper Red Team exercise, the objective is to reach the target by any means necessary.
The Mandatory Criteria of a TLPT According to DORA
The official definition clarifies the concept, but the technical details are still unclear. Fortunately, Article 26 specifies some mandatory criteria for a Threat-Led Penetration Test:
- The test must cover “several or all critical or important functions” of the financial entity;
- The scope is defined by the entity itself, but must be approved by the competent authorities;
- If third-party ICT services are included in the scope, the entity must take “take the necessary measures and safeguards to ensure the participation” of the service provider involved. Full responsibility remains with the entity.
- Testing must be performed on live production systems;
- A test must be carried out at least every 3 years. The competent authorities may reduce or increase this frequency for a given entity, according to its risk profile or operational circumstances.
- On completion of the test, the financial entity must submit to the competent authorities a summary of the relevant findings, corrective action plans, and documentation demonstrating that the test has been run in accordance with the requirements.
- In return, the authorities issue an attestation in order “to allow for mutual recognition of threat-led penetration tests between competent authorities”.
TIBER-EU Framework and ESAs’ Standards to Guide Operational Requirements
While DORA lays down the guidelines for Threat-Led Penetration Testing, it is another European framework that guides operational requirements: TIBER-EU. It is currently being implemented in various EU countries, with the ambition of applying to all. For instance, there’s TIBER-BE for Belgium, TIBER-LU for Luxembourg, TIBER-DK for Denmark, and so on.
TIBER-EU specifies a number of criteria, such as the scope of the test or the methodologies and approach to be followed for each phase, from construction to remediation. It also details the requirements applicable to Threat Intelligence and Red Teaming service providers involved in test execution. It should be noted that there is currently no recognized certification for TIBER-EU test providers, a matter which should be clarified at European level over the coming months.
Regarding TLPTs, DORA gives the European Supervisory Authorities (ESAs) responsibility for developing regulatory technical standards, based on the TIBER-EU framework. The first version of these standards, still in draft phase, was published in November 2023, and will be submitted to the European Commission on July 17, 2024.
The same draft also specifies that countries that have already adopted the TIBER-EU framework may continue to use it. It should soon be amended to reflect certain measures introduced by the ESAs.
In this article, we will discuss the compliance aspects that we consider the most essential. But if you’d like to know all the operational requirements of a TLPT, we can only recommend that you read:
- The draft Regulatory Technical Standards specifying elements related to Threat-Led Penetration Testing, published by the ESAs;
- the TIBER-EU information page published by the ECB;
- the TIBER-EU framework guidelines for the provision of Threat Intelligence and Red Teaming services.
We also advise you to consult the national transposition of the TIBER framework in your country, if available. To date (January 2024), 16 countries have published a national implementation guide — Austria, Belgium, Denmark, Finland, France, Germany, Iceland, Ireland, Italy, Luxembourg, the Netherlands, Norway, Portugal, Romania, Spain and Sweden.
Which Financial Entities Are Affected by TLPT?
Well, it’s quite simple: it’s up to the competent authorities to decide! Article 26(8) of DORA gives them the duty to “identify financial entities that are required to perform TLPT […] based on an assessment of the following:” (list true to the original text)
- impact-related factors, in particular the extent to which the services provided and activities undertaken by the financial entity impact the financial sector;
- possible financial stability concerns, including the systemic character of the financial entity at Union or national level, as applicable;
- specific ICT risk profile, level of ICT maturity of the financial entity or technology features involved.
Competent authorities must apply the principle of proportionality when deciding which entities are subject to advanced testing.
Clearly, the factors put forward by DORA, which are qualitative in nature, do not make it possible to say precisely who should or shouldn’t carry out a Threat-Led Penetration Test. Fortunately, the ESA’s draft Regulatory Technical Standard (RTS) goes way further.
Read also: DORA: A complete guide to compliance for the financial sector
Identification Based on a Two-Level Approach
The ESA’s RTS introduce a two-layer approach to the identification of financial entities required to carry out a TLPT:
- Specific criteria and thresholds are defined for financial entities operating in the main sub-sectors of finance, and playing a systemic role;
- Other criteria are specified so as to give the competent authority the option of including other financial entities which do not operate in a vital sub-sector but still meet the said criteria.
It should be stressed here that, while the competent authority can include entities in the TLPT obligation at will, it can also exclude them. For example, it may decide to exclude regulated entities that are not in a position to do so, or that do not have a certain degree of systemic importance, and that are not technologically mature enough not to risk jeopardizing the continuity of core financial services.
The Complete List of Entities Required to Carry Out TLPTs
As mentioned earlier, entities operating in a major sub-sector of the financial world, and which play a systemic role, are required to carry out TLPTs. Now, the question is: what are these sub-sectors?
Here, it’s Article 2 of the draft ESA regulatory technical standards that we need to turn to. Rather than paraphrasing, we provide you with the list of entities concerned as it stands.
TLPT authorities shall require all of the following financial entities to perform TLPT:
- Credit institutions identified as global systemically important institutions (G-SIIs) in accordance with Article 131 of Directive 2013/36/EU of the European Parliament and of the Council or as other systemically important institutions (O-SIIs) or that are part of a G-SIIs or O-SIIs;
- Payment institutions, exceeding in each of the previous two financial years EUR 120 billion of total value of payment transactions as defined in point (5) of Article 4 of Directive (EU) 2015/2366 of the European Parliament and of the Council;
- Electronic money institutions, exceeding in each of the previous two financial years EUR 120 billion of total value of payment transactions as defined in point (5) of Article 4 of Directive (EU) 2015/2366 or EUR 40 billion of total value of the amount of outstanding electronic money;
- Central securities depositories;
- Central counterparties;
- Trading venues with an electronic trading system that meet at least one of the following criteria:
- at national level, the trading venue which has the highest market share in terms of turnover in equity, or in equity-like, financial instruments or in bonds and other forms of securitised debts, or in derivative contracts or in other non-equity financial instruments in each of the preceding two financial years;
- at Union level, the trading venue whose Union market share in terms of turnover in equity, or in equity-like, financial instruments or in bonds and other forms of securitised debts or in derivative contracts or in other non-equity financial instruments exceeds 5% in each of the preceding two financial years; where the trading venue is part of a group, the turnover of financial instruments on all trading venues pertaining to the same group and established in the Union shall be considered.
- Insurance and reinsurance undertakings that meet the following criteria in a subsequent manner, identifying:
- First, the undertakings exceeding in each of the previous two financial years EUR 500 million of Gross Written Premium (GWP);
- Secondly, undertakings that fulfill the previous point included in the 90th percentile of the Gross Written Premiums (GWP) distribution including all undertaking having reported Gross Written Premiums above the average of the Gross Written Premiums of all insurance and reinsurance undertaking established in the Member State calculated separately for the following activities:
- Life other than life Similar-To-Health (SLT) and reinsurance life;
- Non-Life other than non-life Similar-To-Health (NSLT) and reinsurance non-life;
- Health calculated as the sum of life Similar-To-Health (SLT) and non-life Similar-ToHealth (NSLT) and;
- Reinsurance calculated as the sum of reinsurance life and reinsurance non-life.
- Third, insurance and reinsurance undertakings that fulfill point (ii) and whose total assets is equal or higher to the 10 % of the sum of the total assets valuated according to Article 75 of Directive 2009/138/EC of the insurance and reinsurance undertakings established in the Member State belonging to the activity type identified as referred to in the previous point;
Once again, it is important to remember that this list is only the first level of identification of entities subject to the TLPT obligation. The competent authorities are entirely free to designate financial entities other than those mentioned above, on the basis of a set of factors which it would be far too laborious to list here. If you wish to read more about these conditions, please refer to Article 2(3) of the ESA’s draft technical standards for TLPTs.
“Pooled Testing” for ICT Service Providers
It may be that an ICT service provider cannot be included, as this would compromise the security of its services or the quality of the test. Similarly, it may happen that a provider is the supplier of different financial entities. In such cases, DORA allows for an exception.
The provider may conduct a group test involving several financial entities to which it provides its services. The provider must then:
- agree this test in writing with the various entities;
- sign contractual agreements with an external tester;
- ensure that the test covers all ICT services supporting the critical and important functions of the financial entities;
- conduct the test under the direction of a designated financial entity.
In such cases, Article 26(4) states that the pooled test “shall be considered TLPT carried out by the financial entities participating in the pooled testing.”

DORA: A Complete Guide to Compliance for the Financial Sector
A 50-page guide to walk CISOs, DPOs and legal departments through the EU regulation. No mumbo jumbo, only useful and actionable insights.
How Often Should a Threat-Led Penetration Test Be Performed?
As mentioned above, designated financial entities must carry out a TLPT at least every 3 years. Competent authorities may, at their discretion, reduce or increase this frequency for a designated entity, depending on its risk profile or operational circumstances.
What Should Be the Duration of a TLPT?
This question is difficult to answer precisely, as the duration of a TLPT will depend on its scope and the complexity of the entity targeted. Nevertheless, the ESAs’ draft technical standards provide for various deadlines which, taken together, make it reasonable to expect a TLPT to last from 6 to 12 months.
For example, the scope specification document must be returned to the TLPT authority within six months of receipt of the obligation to carry out a test. As for the active testing phase (Red Teaming), it must not be shorter than 12 weeks. We’ll come back to the details of each phase in a moment.
Who Are the Stakeholders in a TLPT?
The ESA’s draft RTS foresees five participants for a TLPT under DORA:
- The TLPT Cyber Team;
- The Control Team;
- The Blue Team;
- The Threat Intelligence (TI) provider;
- The Red Team.
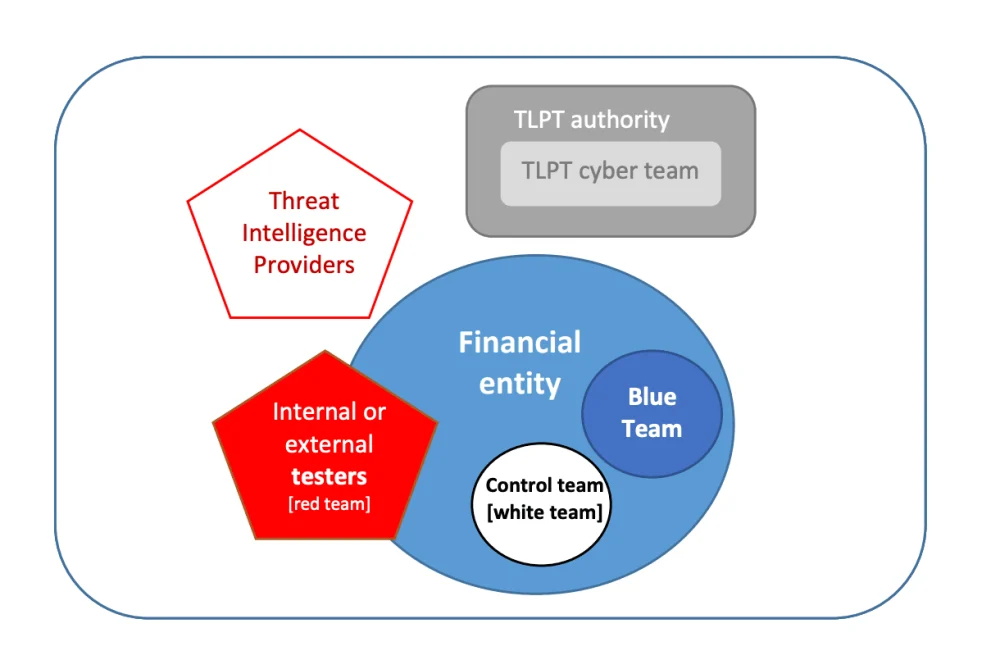
threat led penetration tests, European Supervisory Authorities (ESAs), 27 November 2023.
The TLPT Cyber Team
The TLPT Cyber Team is an internal team of the regulator, aka the TLPT authority. At least two test managers must be assigned to each TLPT, one principal and one alternate.
The Control Team
The Control Team is an internal team within the financial entity being tested, and appointed by it. It is responsible for ensuring liaison with the regulator’s TLPT Cyber Team, and for everything related to the proper completion of the exercise — management of external service providers, risk assessment, day-to-day operational management of testing activities, risk management, etc.
The Control Team must have the necessary mandate within the financial entity to guide all aspects of the TLPT without having to disclose its content to other teams. It should be as small as possible in order to reduce the risk of leakage.
The Blue Team
The Blue Team is the financial entity’s defensive security team — the SOC for example. The Blue Team must not be informed of the existence of the TLPT until the end of the active testing phase.
The Threat Intelligence Provider
The Threat Intelligence (TI) provider is an external service provider responsible for carrying out threat intelligence missions — quite obvious, isn’t it?
The Red Team
The Red Team is made up of the testers who will carry out the attacks as part of the TLPT. These testers may be external or internal to the entity, provided certain conditions are met, to which we’ll come back later.
It is worth pointing out that the ESAs’ draft RTSt prefers to use the term “testers” in its broadest sense, rather than “Red Team” in the sense of the TIBER-EU framework, which is stricter regarding the choice of Red Team members. For example, the TIBER-EU framework doesn’t authorize the use of in-house testers — a point which should be amended in the near future.
What Are the Different Phases of a TLPT?
In order to find out more about the different stages of a Threat Led Penetration Test (TLPT), once again we have to look at the ESAs’ draft RTS.
A TLPT consists of three main phases:
- The preparation phase;
- The testing phase;
- The closure phase.

threat led penetration tests, European Supervisory Authorities (ESAs), 27 November 2023.
The Preparation Phase
It’s during this phase that the entity under testing must form its internal Control Team, and choose its Threat Intelligence and Red Teaming providers — unless the testers are internal, of course. The scope of the TLPT must be defined, as well as its code name and the communications channels to be used.
The full content of the preparation phase is detailed in Article 6 of the draft ESAs’ RTS.
The Testing Phase
The testing phase is divided into two parts:
- the first part, dedicated to the Threat Intelligence scenarios;
- the second one, dedicated to the execution of these scenarios by the Red Team.
The Threat Intelligence Phase
The testing phase begins with the production of the Threat Intelligence scenarios to be used during the TLPT. The threat intelligence provider must propose several scenarios, which differ according to the threat actors identified and the associated tactics, techniques and procedures, and must target each of the critical or important functions.
Three scenarios are to be selected by the Control Team, based on:
- the recommendation by the threat intelligence provider and the threat-led nature of each scenario;
- the input provided by the test managers;
- the feasibility of the proposed scenarios for execution, based on the expert judgment of the testers;
- the size, complexity and overall risk profile of the financial entity and the nature, scale and complexity of its services, activities and operations.
These scenarios must be compiled into a Threat Intelligence report, which must be sent to the TLPT authority for validation.
The Red Teaming Phase
Once the choice of scenarios has been made, it’s time to move on to the active testing phase, i.e. Red Teaming.
Testers must draw up a “Red Team Test Plan”, which is basically a detailed plan of the attacks to be carried out. This plan must, of course, be based on the scope specification document, and on the TI scenarios selected. The exact content of this plan is detailed in Appendix IV of the ESAs’ draft standards, which we recommend you consult.
The Red Team test plan must be validated by the entity’s internal Control Team, as well as by the TLPT authority.
Next comes the active testing phase — the execution of the attacks — which must be proportionate to the scope and complexity, and last a minimum of 12 weeks.
Throughout the active testing phase, testers must report at least once a week to the Control Team and the TLPT Cyber Team on the progress of the operation. The test can only be brought to an end with the agreement of all parties involved — the internal Control Team, the testers, the TI provider and the TLPT authority.
The full content of the testing phase is detailed in Article 7 of the ESAs’ draft RTS.
The Closure Phase
The closure phase begins at the end of the active testing phase, and consists mainly of the drafting of various reports, and joint exercises between the Red Team and the Blue Team, the financial entity’s defensive security team. This is when — and not before — the existence of the TLPT is revealed to the Blue Team.
A Red Team Report
Within four weeks of the end of the testing phase, the attacking team must send a Red Team report to the Control Team, which must forward it without delay to the Blue Team. The exact content of the Red Team report is detailed in Appendix V of the draft AES standards.
A Blue Team Report
Within four weeks of receiving this report, the defensive team must in turn draw up a Blue Team report, which is provided to the Control Team, then forwarded to the attacking team and the TLPT Cyber Team managers. The exact content of this Blue Team report is detailed in Appendix VI of the draft AES standards.
Purple Teaming and Final Report
Then, within four weeks of the previous step, the Red Team and Blue Team must meet to examine the offensive and defensive actions that have been carried out. A Purple Team exercise — a joint exercise between the defense and attack teams — must then be held, under the direction of the Control Team, which will have previously identified the topics to be addressed.
This Purple Teaming can include methods such as tabletop exercises, catch-and-release exercises, war games or the joint development of proofs of concept (PoC) for selected TTPs.
Finally, the Control Team must prepare a summary report of the TLPT and its conclusions, which must be sent to the TLPT authority within a maximum of 12 weeks after the end of the testing phase. The exact content expected of this final report is detailed in Appendix VII of the ESAs’ draft standards.
Remediation Plans
Remediation plans must also be sent to the TLPT authority by the Control Team within 16 weeks of the end of the active testing phase.
These remediation plans must include:
- a description of the identified shortcomings;
- a description of the proposed remediation measures and of their prioritization and expected completion, including where relevant measure to improve the identification, protection, detection and response capabilities;
- a root cause analysis;
- the financial entity’s staff or functions responsible for the implementation of the proposed remediation measures or improvements;
- the risks associated to not implementing the above measures and, where relevant, risks associated to the implementation of such measures.
Finally, the TLPT authority must issue a TLPT certificate to the financial entity, specifying which critical systems were included in the scope.
The full content of the closure phase is detailed in Article 9 of the ESAs’ draft RTS.
In-House or Outsourced Testing?
There’s one question we haven’t yet addressed concerning TLPT: should testing be outsourced, or can it be carried out in-house? Short answer: it depends.
Article 26.8 of DORA allows financial entities to rely on in-house testers, but also introduces an obligation to call in an external tester every third test. The ESAs’ RTS specify that if the Red Team is made up of a mix of internal and external testers, the TLPT is considered to have been conducted with internal testers.
One important exception: credit institutions classified as significant must always turn to an external tester.
An Obligation to Use an External Tester for Significant Credit Institutions
This same Article 26.8 of DORA stipulates that “credit institutions that are classified as significant in accordance with Article 6(4) of Regulation (EU) No 1024/2013” have no choice but to call in external testers. Now, the real question is: What is a significant credit institution within the meaning of Regulation (EU) n°1024/2013?
The text in question assesses significance according to three criteria:
- the size of the institution;
- its importance for the economy of the Union or of a participating Member State;
- the importance of its cross-border activities.
In practical terms, a credit institution is considered significant if one of the following three conditions is met:
- the total value of the institution’s assets exceeds 30 billion euros;
- the ratio between its total assets and the GDP of the Member State in which it is established is greater than 20%, unless the total value of its assets is less than 5 billion euros;
- the ECB designates it as such on its own initiative, in which case the institution receives notification from its national competent authority.
If a credit institution meets at least one of these conditions, it is not authorized to carry out TLPTs with an internal tester.
It may seem paradoxical that such organizations should be forced to outsource, even though they possess the most substantial resources — both financial and human — which would allow for in-house testing. The main reason for this is the desire for greater, impartial supervision of the banking institutions that are essential to the health of the European financial system.
This Regulation (EU) n°1024/2013 quoted by DORA, the one that sets out what a significant credit institution is, was born in the wake of the public debt crisis within the eurozone (2010-2012), itself a knock-on effect of the subprime crisis. Its primary objective was to entrust supervisory powers to an omnipotent third party, in this case the ECB, without any considerations other than prudential ones being involved. In fact, the official name of this legislation is: “Regulation conferring specific tasks on the European Central Bank concerning policies relating to the prudential supervision of credit institutions”. Crystal clear, isn’t it?
DORA thus echoes Regulation no. 1024/2013, requiring significant credit institutions to use external testers of the highest quality in order to avoid conflicts of interest or motivations other than security when performing a TLPT.
The Conditions to Be Met to Carry Out a TLPT With In-House Testers
Article 27.2 of DORA sets out the conditions that entities must meet when resorting to in-house testers:
- The use of in-house testers has been approved by the relevant competent authority (or by the single public authority designated);
- The financial entity has sufficient resources to conduct a TLPT, and has taken care to avoid conflicts of interest throughout the design and execution phases of the test, both of which must be verified by the competent authority;
- The Threat Intelligence provider is external to the financial entity. That means that all Threat-Intelligence assignments must be outsourced.
In addition, Chapter IV of the ESAs’ draft regulatory technical standards specify and reinforce the requirements governing the use of in-house testers.
To be authorized to use their own testers as part of a TLPT, regulated entities must — in addition to the previous requirements —:
- define and implement a policy for the management of internal testers in a TLPT. Such policy shall:
- include criteria to assess suitability, competence, potential conflicts of interest of the testers and define management responsibilities in the testing process. The policy shall be documented and periodically reviewed;
- provide that the internal testing team includes a test lead, and at least two additional members. The policy shall require that all members of the test team have been employed by the financial entity or by an ICT intra-group service provider for the preceding two years;
- include provisions on training on how to perform red teaming of the internal testers.
- define measures to ensure that the use of internal testers to perform TLPT will not negatively impact the financial entity’s general defensive or resilience capabilities regarding ICT-related incidents or significantly impact the availability of resources devoted to ICT-related tasks during a TLPT.
The use of in-house testers must also be mentioned in three documents: the test preparation document (during the preparation phase), as well as the Red Team test report and the TLPT summary report (during the closure phase).
Finally, it should be noted that testers employed by an intra-group service provider are considered as internal testers of the financial entity.
How to Choose a Service Provider to Perform a TLPT?
As mentioned earlier, financial entities must involve an external tester at least once every three tests. This raises the question of selecting the service provider.
Requirements Applicable to External Testers
Article 27 of DORA defines the requirements applicable to testers who may perform a Threat-Led Penetration Test.
To be authorized to carry out TLPTs, external testers must :
- be of the highest suitability and reputability;
- possess technical and organizational capabilities and demonstrate specific expertise in threat intelligence, penetration testing and red team testing;
- be certified by an accreditation body in a Member State or adhere to formal codes of conduct or ethical frameworks;
- provide an independent assurance, or an audit report, in relation to the sound management of risks associated with the carrying out of TLPT, including the due protection of the financial entity’s confidential information and redress for the business risks of the financial entity;
- be duly and fully covered by relevant professional indemnity insurances, including against risks of misconduct and negligence.
To these conditions must be added those of the ESAs’ draft technical standards, Article 5 of which lays down additional requirements for the selection of external testers:
- The external testers must provide at least five references from previous assignments related to intelligence-led red team tests;
- Red Team staff assigned to the TLPT must:
- be composed of at least the a manager, with at least 5 years of experience in threat intelligence-led red team testing as well as at least two additional testers, each with red teaming experience of at least 2 years;
- display a broad range and appropriate level of professional knowledge and skills, including, knowledge about the business of the financial entity, reconnaissance, risk management, exploit development, physical penetration, social engineering, vulnerability analysis, as well as adequate communication skills to clearly present and report on the result of the engagement;
- have a combined participation in at least five previous assignments related to threat intelligence-led red team tests.
Data Processing Must Be Secure
It goes without saying that, when working with an external service provider, financial entities need to ensure that their data is in safe hands. After all, the very nature of TLPTs means that the external tester is likely to be dealing with information that is sensitive, if not highly confidential.
Article 27.3 of the Digital Operational Resilience Act addresses this issue head-on:
“Financial entities shall ensure that contracts concluded with external testers require a sound management of the TLPT results and that any data processing thereof, including any generation, store, aggregation, draft, report, communication or destruction, do not create risks to the financial entity.”
An On-Premise Platform to Guarantee Data Security
To address this data governance issue, we propose two types of deployment of the Yogosha platform for resilience testing and TLPT:
- SaaS: a turnkey solution, hosted via 3DS Outscale and its SecNumCloud-certified sovereign cloud (the highest French security standard, established by the French CERT). Data is hosted on French soil.
- Self-Hosted: a solution designed for organizations with the most stringent security requirements. You’re free to host the Yogosha platform wherever you like — private cloud, on premise — to retain total control over your data and the execution context. In this way, all data associated with the realization of a TLPT remains in your possession, from start to finish.
In both cases, the intrinsic robustness of our product is at the heart of our concerns. We continually secure our assets through a DevSecOps pipeline, OWASP guidelines, recurrent penetration testing and an ongoing bug bounty program. We are also in the process of obtaining ISO 27001 certification for our platform.
Yogosha as a TLPT Red Teaming Provider
As a reminder, the requirements applicable to third-party testers in the context of a Threat-Led Penetration Test are set by:
- Article 27 of DORA;
- and the regulatory technical standards expected from AES and ECB, themselves based on the TIBER-EU framework, which defines the requirements for Threat Intelligence and Red Teaming providers.
We are already taking the necessary steps to meet all these requirements — legal, technical and operational. The deeply unique, complex and confidential nature of such large-scale testing makes it difficult for us to expand publicly on all aspects, nor can we disclose the content of our Red Teaming services, i.e. our testers, methodologies and operational aspects. We therefore invite you to contact us to discuss your TLPT requirements in greater detail.
46 Questions to Ask a Potential Red Teaming Provider, According to TIBER-EU
Nevertheless, you should know that there is a list of 46 questions that the TIBER-EU framework suggests financial entities to ask Red Teaming providers during the selection process.
We’ve taken the test, and Yogosha can already answer 41 of the 46 questions positively — and we’re actively working to satisfy the others.
If you’d like to consult this list, along with our detailed answers, please download the PDF of this guide at the top of this page.
Carrying out a Threat-Led Penetration Test is no mean feat. It’s a long-term exercise, involving a significant workload and expense for the CISOs and security teams of regulated entities.
It is essential to prepare as well as possible before undertaking a TLPT, in order to maximize your chances of success. This is precisely the subject of the fourth and final chapter of this guide to security testing for entities regulated by DORA:





