Table of Contents
The Vulnerability Operations Center is a platform. One that allows customers to combine three elements to detect and manage vulnerabilities:
- a technology
- an access to skilled resources
- a convergence of security operations
By connecting these three elements, the VOC provides a genuine technological solution that enables customers to efficiently deal with the vulnerability reports they face on a daily basis.
The VOC is to offensive security what the SOC is to defensive security.
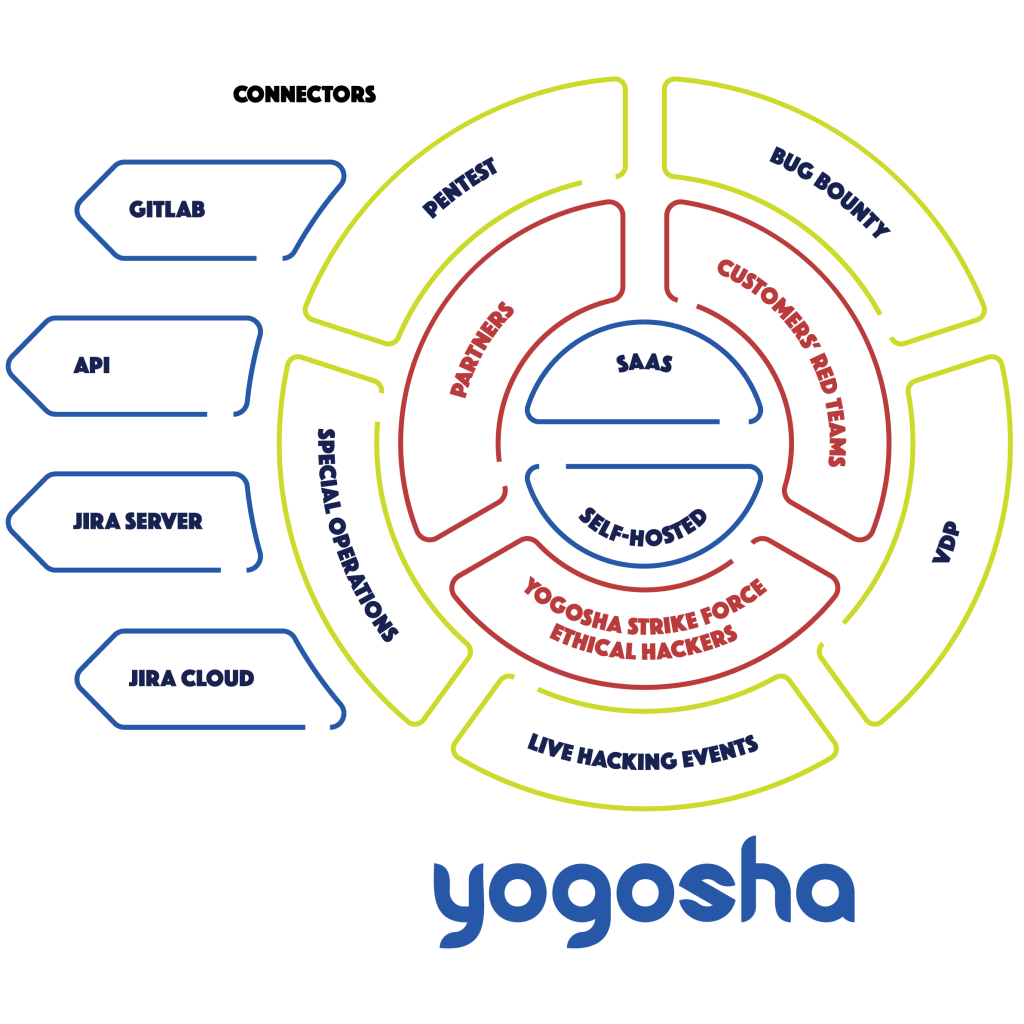
1. First, the VOC is a technology.
This means a platform with easy-to-use interfaces and a user experience that respects market standards. And above all, a platform that meets regulatory compliance.
If the customer is at ease with a SaaS deployment, he can go with that. If he wants to have a platform hosted by a trusted hosting provider, or even On Prem, he must have this possibility nowadays. So, that’s the first element of the VOC. A technology, a SaaS or Self-Hosted platform.
Self-Hosted deployment allows customers to have:
- a strong data isolation
- full control of their execution context, and compliance assurance that the data is hosted in a fully controlled environment
- a centralization of all their security activities on the same platform, even if they are carried out across several entities
- a tool branded with their own colors and that naturally integrates into their solution portfolio, or even that can be resold to end customers if relevant.
2. Second, the VOC is a direct access to skilled resources.
Once we have this first layer – this platform that can be deployed wherever we want it – the customer must be able to bring on board the different communities that enable him to find security weaknesses. This is the purpose of the VOC as we built it.
There are four main groups behind these communities.
- Ethical hackers from the Yogosha Strike Force, our historical community. They are highly skilled hunters, who are carefully selected and are experts at finding high-risk vulnerabilities.
- The client’s own security teams.
- Its partners’ teams. If a customer has a partner who has red teamers or pentesters, he can bring them onto the platform.
- The customer’s technical teams, such as the developers.
The VOC brings together these different disciplines, and helps all these people to communicate with each other.
3. Finally, the VOC allows a convergence of security operations.
The Yogosha VOC provides four main types of services. These security operations are :
- Bug Bounty
- Vulnerability Disclosure Program (VDP)
- Penetration Testing as a Service
- Live Hacking Event
Penetration Testing as a Service
Penetration testing is a standard. Whenever you have a system somewhere, you have to do regular security audits. The penetration test is a security audit with a logic of means.
It provides expertise over a determined period of time, with the objective of conducting the most exhaustive security tests possible to give a complete picture of the IT system at a given point in time. The goal is to identify potential areas of fragility and security weaknesses.
The Yogosha VOC to digitalize and streamline penetration tests
The VOC brings consistency to this process. We make this classic exercise more fluid ; we digitalize the penetration tests that customers are already used to conducting.
The VOC also makes it possible to meet a timing requirement. Some companies have to put applications into production very quickly, to meet a Go-to-market deadline or for some other reason. But their traditional penetration tests can only be activated after several months because the provider has no bandwidth. Here, the Yogosha Strike Force becomes a real alternative to quickly find skills for this kind of audit.
In a nutshell, Pentest as a Service is :
- a one-time resource
- on a fixed time basis
- charged on a pro-rata basis of the research time spent
- with the objective of having a global and methodical overview to reveal security weaknesses.
Bug Bounty
Bug Bounty is a much more opportunistic and aggressive approach.
When a customer reaches a sufficiently advanced state of security, penetration tests show their limits. Bug bounty then allows to face reality, by asking hackers to test the security of the system.
It is an audit with a new operating mode. There is no time limit, the only limit is the allocated budget. Where pentesting pays for the time spent searching, bug bounty pays for the vulnerability found. The price is indexed to the criticality of the vulnerability. As long as the customer has a budget, he can ask hackers to continue testing his system.
With bug bounty, we are on a logic of results. To oversimplify, if the hackers don’t find anything, the customer doesn’t have to pay anything.
Vulnerability Disclosure Program (VDP)
A Vulnerability Disclosure Program (VDP) is something entirely different. It is a company policy that clarifies the terms under which it can collaborate with unsolicited people who have found security gaps in their systems.
With a bug bounty or a pentest, it is the company that asks hackers to test its security. With a VDP, the company doesn’t ask anyone for anything. It is the hacker who – while monitoring and researching – finds a vulnerability in the company’s systems.
If the company doesn’t have a VDP, the hacker can try to talk to the community manager on Twitter, to find the CISO on social networks… But it’s always a process that borders on bad buzz and that puts the teams under tension.
Having a VDP frames this exercise. It allows the company to say to the hacker: “We are ready to work with you if you respect these rules. Here’s the modus operandi. This is how you can report back to us. Here’s the response time you can expect. And here is our compensation policy, if there is compensation.”
With a VDP, the research of a breach is not solicited. So, in theory, there is no need to pay the hunter. In reality, the company is free to reward the hacker or not as a sign of gratitude – taking into account, for example, the criticality of the vulnerability.
Live Hacking Event
With the Live Hacking Event, we are on a double exercise.
First, a training session for the client’s teams.
The idea is to bring hackers on site for 2-3 days (or more) with the client’s teams to do some bug bounty. So there is a real training aspect, we simulate a Red Team vs Blue Team configuration. The client’s teams are almost in a real situation, they are confronted with the attack.
The Live Hacking Event is an opportunity for the teams to discuss and bond, to have informal discussions with hackers. The exchanges are not of the same nature as what we can have by comments through the platform. It’s much more vivid, it makes an impression.
Secondly, a communication tool.
The Live Hacking Event allows companies to show:
- that they are serious about working with hackers
- that they have an innovative approach to cybersecurity
The Live Hacking Event then becomes a real recruitment lever for security teams ; and this is no mean feat when you consider the skills shortage that exists in these professions. The practice shows that the environment is quite dynamic. When you have a background in security, it’s nice to know that you’re going to work for a company where, once a year, you’re going to be totally immersed in protecting systems against 150 hackers who are trying to attack it!
Who is the VOC for?
The VOC can be useful to different profiles, or even become indispensable to them.
First, the CISO. The VOC allows CISOs to converge their different services and to have a unique hub through which they can supervise all their activities. The VOC also allows internal teams – developers, for example – to see how the systems’ security evolves over time.
The VOC can also be used by companies that can offer it to their customers themselves. System Integrators and MSSPs for example, who can leverage our expertise and technology in Self-Hosted to :
- digitalize their own services
- bring added value to their customers
- generate additional revenue streams
For these profiles, we offer specific partner programs.
To conclude
To conclude, VOC is the result of a strong belief. On the one hand, customers need all their offensive operations in one place. On the other hand, they absolutely must have a choice in the level of services they want to have – from deployment to operations and the communities they want to work with.
Behind the concept of the Vulnerability Operations Center, there are a multitude of features to ease the detection and management of vulnerabilities. If you would like a demonstration of the VOC, please contact us.



