Table of Contents
With the exponential growth in volume and sophistication of cyberattacks, further fueled by AI, organizations are looking increasingly for ways to rapidly raise their Security Posture. The most common practice is to use Vulnerability scanners to perform Vulnerability Assessments (VA) in order to uncover potential vulnerabilities that require further validation and/or remediation.
However, relying solely on Common Vulnerabilities and Exposures (CVEs) and Automated Scanners can leave organizations exposed to significant risks. While CVEs provide a valuable foundation for vulnerability management, they often fall short in addressing the dynamic nature of threats and the nuances of real-world exploitation.

Before we dive deep into this, first a few words about the limitations and concerns of using CVEs and Automated Scanners.
- Delayed Vulnerability Discovery: CVEs are often published after vulnerabilities have been discovered and exploited in the wild. This delay can leave organizations vulnerable to attacks before they are even aware of the threat.
- Incomplete Vulnerability Coverage: CVEs frequently focus on software vulnerabilities but may not adequately address hardware vulnerabilities, configuration errors, or emerging attack vectors.
- Sophisticated Vulnerabilities not found. Scanners can only look for what they are told to look for. More complex vulnerabilities such as logical flaws, breach insertions in business processes, and authorization bypasses can typically not be found this way.
- False Positives and Negatives: Automated scanners can generate long lists of false positives vulnerabilities without validation and documentation, leading to lot of noise and unnecessary remediation efforts, or false negatives and missing critical vulnerabilities.
- Lack of Contextual Understanding: CVEs and scanners often fail to provide the context needed to prioritize vulnerabilities based on their potential impact, exploitability, and the organization’s specific risk profile.
Looking Back at 2024’s CVE Landscape
The year 2024 has come and gone, leaving in its wake a trail of digital breadcrumbs in the form of Common Vulnerabilities and Exposures (CVEs). It is a good time to reflect on the cybersecurity landscape marked by unprecedented growth in vulnerabilities and shifting trends that have reshaped how organizations approach security.
Surprisingly the number of vulnerabilities continue to grow rather than decline as one would expect after discovery and remediation. How did the number of reported vulnerabilities then trend upward and why, and what were the most prevalent types of vulnerabilities discovered? This will help security professionals, security researchers, and organizations alike to prepare for the evolving threat landscape and proactively fortify its defenses.
Insights in these key statistics, trends, and notable vulnerabilities shared below will help us augment our security strategies in the year ahead and continue the trend towards more sophistication and embeds a Continuous Offensive Security Testing approach.
Vulnerability Inflation: The Rising Tide of Cybersecurity Threats
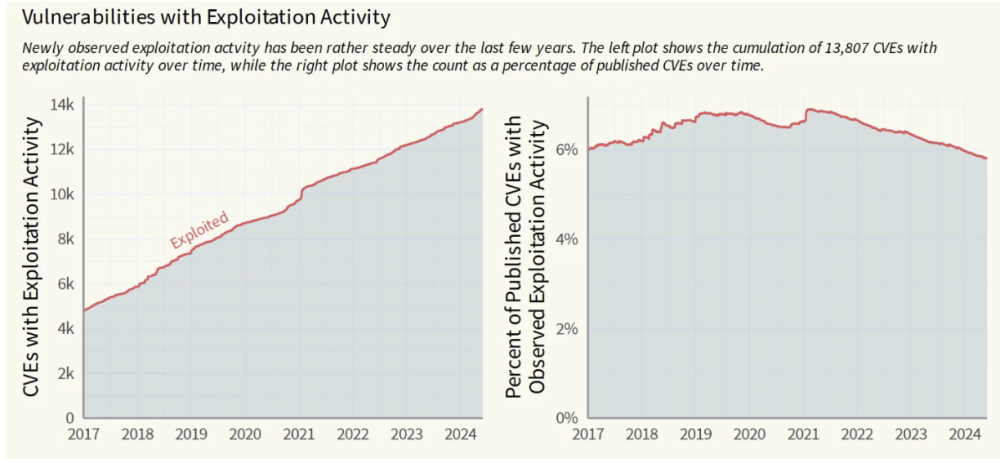
As of May 31, 2024, 237,687 CVEs have been published, with 13,807 (5.8%) observed in active exploitation. This data reveals critical insights into the evolving vulnerability landscape and the challenges of prioritization in a world of “CVE inflation.”
In 2024, the cybersecurity landscape witnessed a staggering 40,009 vulnerabilities published—a 38.83% increase from the 28,818 CVEs reported in 2023.

This exponential growth mirrors a phenomenon akin to financial inflation, where the increasing volume of vulnerabilities dilutes the overall security posture of organizations. Just as an oversupply of currency devalues its worth, the sheer number of vulnerabilities can overwhelm Security Teams, leaving critical systems exposed and undermining the effectiveness of traditional cybersecurity measures.
Key Statistics
| Key Metric | Value |
| Total Published CVEs | 237,687 |
| Exploited CVEs | 13,807 (5.8% of total) |
| CVEs Published in Last 12 Months | >30,000 |
| Average Annual Growth Rate | ~16% |
CVE Exploitation Timelines – from CVE to Attack
While these statistics provide valuable insights, they don’t answer the critical question: How much time expires before PARTICULAR vulnerabilities were exploited?
Pre-Publication Exploitation: 8% of CVEs are already exploited.
It shows that about 8% of all known and exploited vulnerabilities were targeted before the CVE was actually published! This Explain why organizations cannot rely solely on CVE publication dates to gauge risk. Some vulnerabilities are already being exploited before they even appear on the radar.
Within One Month: 40% of all CVEs are exploited.
- Fast exploitation: Within just 30 days of publication , 40% of CVEs observed exploitation in the wild. Example: Vulnerabilities in pre-disclosure phases (e.g., zero-days used in targeted attacks).
- Why it matters: Attackers move quickly to weaponize newly disclosed vulnerabilities. This underscores the importance of prioritizing high-risk CVEs for immediate remediation. Example: Critical flaws like ProxyLogon (CVE-2021-26855) were weaponized within 48 hours.
Within One Year: 70% of all CVEs are exploited
- Majority Exploited Quickly: A strong majority (70% ) of vulnerabilities see their first wave of attack activity within one year of publication.
- Leveling Off: After the one-year mark, the rate of new exploitation slows significantly. Only 7% of published CVEs go three years or more before being exploited.
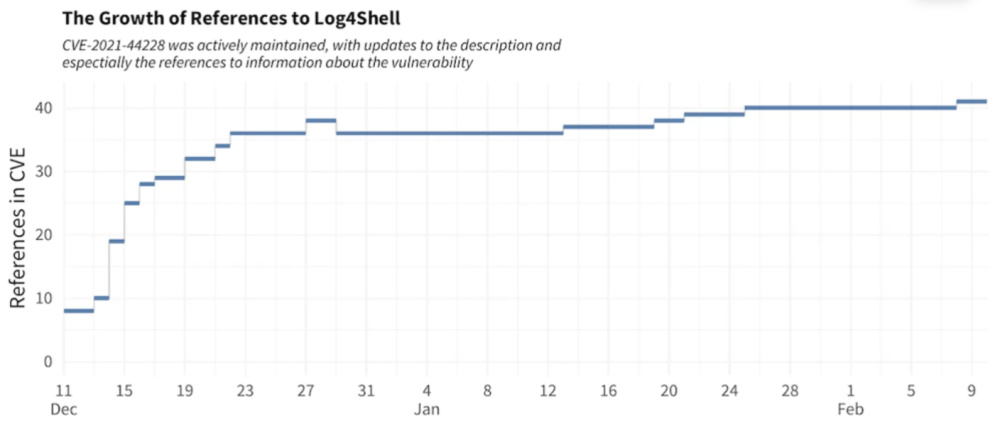
- Example: Log4Shell (CVE-2021-44228) remains widely exploited years later.
Long-Tail Exploitation: 7% of all CVEs after 1 year
- Some rare vulnerabilities remain dormant for years before being exploited. This highlights the importance of maintaining vigilance over older vulnerabilities, especially in legacy systems.
- Only 7% of exploited CVEs saw attacks 3+ years post-publication. For example EternalBlue (CVE-2017-0144) still fuels ransomware in 2024.
Key Takeaways
- No One-Size-Fits-All. 8% of CVEs are “already burning” and over 40% are “fire hazards.” This implies that a more Continuous and offensive (read: adversarial) security testing would be required to proactively uncover which of these are exploitable.
- Time Matters, but Risk Matters More. There is a window of opportunity to stay ahead of potential attackers by focusing on and prioritizing CVEs with high Exploitability, not just “critical” CVE scores which may not reflect risk exposure.
- Legacy Risks Persist. Not to forget is the legacy CVEs that may be older (e.g., 3+ years) but can still lead to a lot of harm and can resurface in attacks. Hence Vulnerability Assessments and Scanners to detect such long-tail potential breach points.
25 Years of CVEs: A Celebration of Data, Not Necessarily Security
The CVE industry method has reached a milestone: 25 years of tracking vulnerabilities! While this achievement is worth celebrating, it’s also a moment to reflect on what the data really tells us—and what it doesn’t. Vulnerability counts are up but that doesn’t tell the full story. Here is a quick and comic insight into a few projects that helped raise the CVE volume.
Why The Current CVE System Is Problematic
Researchers are incentivized to report anything labeled as a CVE, even if it lacks real-world exploitability. Many Organizations already struggle with CVE overload (40,009 in 2024) and some even turn off their Vulnerability Scanners because of the noise it creates. In addition, adding non-exploitable “vulnerabilities” like Node Js demonstrate a bad example of 2025 CVE records and time-to-dump CVEs and their misleading severity that does more harm than good.
Here is a good example: the recent publication of CVE-2025-23088, an End-of-Life (EOL) announcement for Node.js, has sparked controversy in the cybersecurity community. While EOL statuses are critical for organizations to track, framing them as CVEs risks undermining the integrity of vulnerability management and opens the door to misuse.
By classifying EOL as a CVE, it creates unnecessary noise and can lead to alert fatigue. Imagine a security analyst sifting through hundreds of CVEs, many of which are simply announcements that a product is no longer supported. This makes it harder to identify and address the real vulnerabilities that pose an immediate threat
It is early in the year, but CVE-2025-23088 might be in line for the worst CVE of the year. A community highlights a growing trend of misusing the CVE system to gamify bug bounty programs or inflate vulnerability statistics. While EOL software is a risk, conflating it with actual vulnerabilities undermines trust in the CVE ecosystem and distracts from real threats.
TAKEAWAY : The rising tide of vulnerabilities will overwhelm VM teams if remediation can’t be prioritized.
Vulnerabilities vs Breach Risk
Automated vulnerability scanners are often seen as the first line of defense, but they are far from a silver bullet. While these tools provide speed and scalability, they fall short in delivering the depth, context, and prioritization needed to effectively manage modern cyber risks. With PtaaS (Penetration Testing as a Service), we understand the limitations of automated scanners and advocate for a more holistic approach to vulnerability management.
The 2024 CVE data paints a clear picture: vulnerability inflation is real, and traditional methods like automated scanners and compliance-focused pentesting are no longer sufficient.
Organizations must adopt a proactive, adversarial, offensive and data-driven approach to manage the growing volume of threats effectively. The challenge is no longer just about vulnerabilities, but about the risk of critical vulnerabilities when left uncovered. How to identify and prioritize vulnerability effectively to stay secure and maintain control. Here’s how you can achieve that:
- Continuous Offensive Security Testing: simulates real-world attack behavior to uncover hidden vulnerabilities. Move from a compliance-based, checklist-driven testing towards mimicking attack behavior and TTPs; a more effective way to uncover serious exploits.
- Risk-Based Prioritization: use asset criticality for remediation prioritization allowing one to focus on what matters most and causes the biggest risk exposure. Focus on your most critical assets and so called crown jewels.
- Automation and Scalability: integrate automated tools seamlessly with real-time threat intelligence which provides insights into active exploitation campaigns helping organizations to understand which vulnerabilities attackers are currently targeting and try to preempt.
- Actionable Insights: provides metrics and necessary KPIs for gathering detailed remediation advice to drive actual remediation combined with retesting workflow to ensure vulnerabilities are correctly and securely fixed and eliminated.
In cybersecurity, the best defense is a good offense. Timely, data-driven triggered actions relying solely on raw CVE counts is no longer enough. By addressing the limitations of traditional vulnerability management and adopting a holistic approach, integrating Asset Criticality, Threat Intelligence, Business Impact, and Environmental Awareness into your Offensive Security Testing strategy, you can cut through the noise and focus on what truly matters.
This holistic approach not only reduces risk but also aligns remediation efforts with your organization’s unique priorities and operational needs. As we navigate an increasingly complex threat landscape, the key to resilience lies in doing things in a smarter manner—because not all vulnerabilities are created equal, and not all risks demand the same response.
Let’s move beyond the numbers and build a future where data drives action. Therefore, organizations can stay ahead of attackers and build a safer future.
About the author
Ali Bawazeer is a well-known security advocate in the global hacking community with many critical CVEs on his name from companies like Microsoft and Google. He is also a regular speaker and provides trainings at industry conferences such as Black Hat, CyberX and BSides. Last but not least he organizes and host industry forums for Offensive Security researchers and ethical hackers.
Currently he is a Technical Director at Yogosha, an Offensive Security Platform company headquartered in Paris, France.
References
https://www.linkedin.com/pulse/identifying-blind-spots-cve-threat-feeds-david-vassallo-vieqf
https://www.cyentia.com/wp-content/uploads/2024/07/EPSS-Exploration-Of-Exploits.pdf




