Table of Contents
Are you absolutely certain your critical assets are being sufficiently tested? Can you prove it?
The Problem: Security Testing is Based on Trust, Not Proof
For too long, the security testing industry has relied on trust. Significant budgets are allocated to Bug Bounty and continuous pentests without tangible proof of the research effort. This creates vast blind spots in a company’s security posture.
The bug bounty model and continuous pentest model are often more event-driven than continuous. This outdated model is especially problematic in a DevOps environment, where new features are regularly deployed. Without exhaustive coverage and proof of in-depth testing, new vulnerabilities can be introduced, exposing the company to major financial and reputational risks. With the continuous growth of attack surfaces, it’s become essential to adopt a different approach.
Yogosha is changing the game with Activity Monitoring, the only platform that transforms trust into certainty through data. You can now ensure that all your assets are tested continuously and in-depth, and precisely manage the performance of your security programs.
It’s time to move from a trust-based model to a proof-based model.
The Solution: Collecting Traffic via VPN
We collect researchers’ traffic when they use the Yogosha VPN. Our intelligent algorithm then processes this data to measure the activity on the tested assets.
Beyond monitored traffic, we can more exhaustively calculate the offensive activity time. This estimate includes the time spent discovering scopes, writing vulnerability reports, and performing tests outside of the VPN. This gives you a complete view of the time researchers spend securing your assets.
Additionally, all test traffic passes through a fixed IP, making it easy to identify tests performed by our community of researchers, which simplifies management and monitoring.
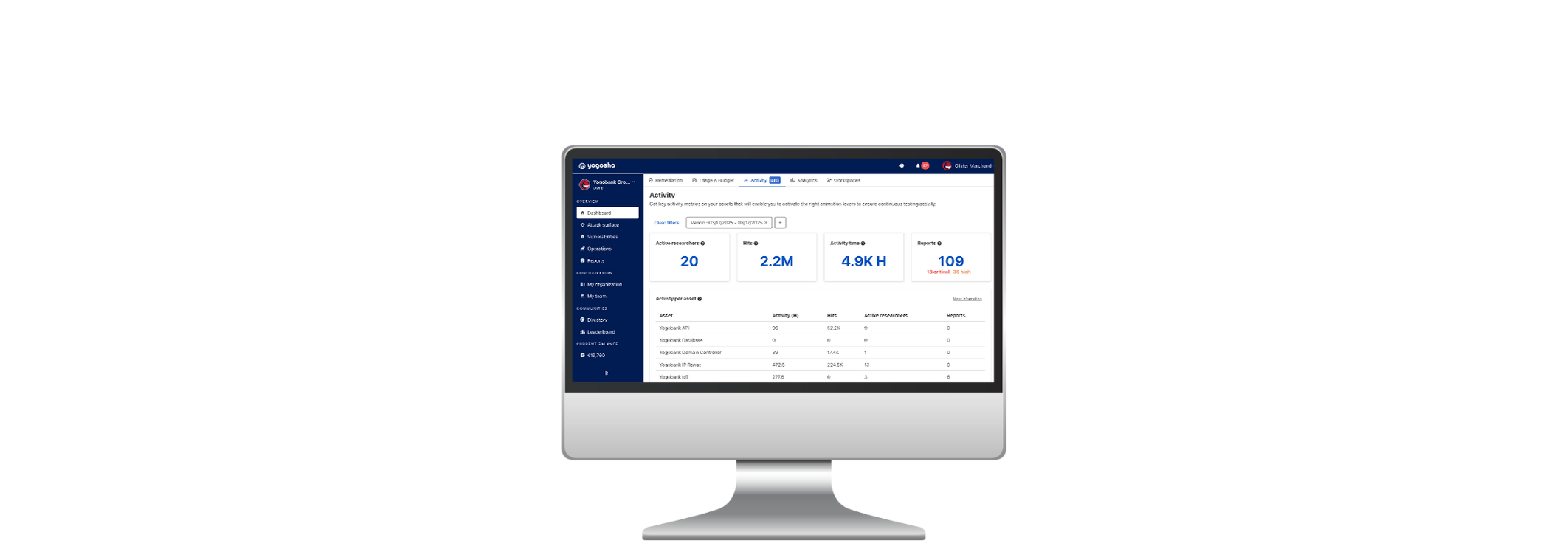
Measure Your Assets’ Activity to Better Secure Them
Yogosha’s Activity Monitoring allows you to precisely measure researcher engagement on your assets and activate the right levers to ensure continuous testing activity. Our dashboard provides complete visibility so you can make informed decisions and ensure flawless security.
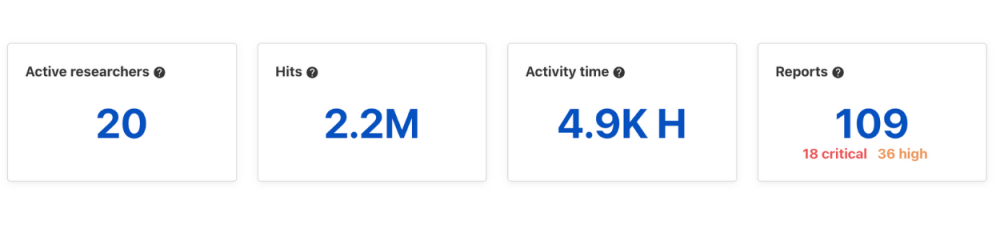
The key indicators are:
- Number of active researchers who have tested your assets.
- Number of hours of offensive activity, including the time estimated by our algorithm for a complete view of the time actually spent securing your assets.
- Number of requests made on your assets’ targets.
- Number of reports received, that you can compare to your activity level vs vulnerabilities found.
And thanks to these key indicators, you can:
- Get an overall view of the activity on your assets.
- View a comparative table of assets with their activity indicators.
- Access daily indicator details to track the impact of your actions or events on the activity level.
Yogosha is the only software provider to offer this level of visibility on the market.
Ensure Continuity and ROI of Your Security Tests
Access to this data allows you to evaluate the level of testing activity on your assets and make informed decisions to continuously improve your security posture.
If the data reveals a drop in activity, you can, with the support of our Security Program Managers and Managed Services team, activate various levers to ensure the continuity of your tests. These levers are :
- Rotating researchers to get a fresh perspective on your assets.
- Increasing rewards to attract more researchers and stimulate competition.
- Updating the testing scope to cover more areas, focus on critical assets, or less-tested areas.
- Launching new operations to target specific assets that were not being tested.
As Mohammed Foudhaili, our Head of Security Programs, points out, this approach offers unprecedented visibility : “Activity Monitoring allows the security program managers on the Yogosha team to have visibility into key indicators, giving them a good measure of the resistance of our clients’ assets to attacks. What’s even better is that it allows them to see which assets and IPs are most tested and which ones need more attention. This way, we can guide researchers to cover more high-risk areas to ensure up to 100% coverage of the attack surface.”
With the visibility in the researcher activity and the ability to activate these different levers, Yogosha allows you to boost testing intensity and maximize the return on investment (ROI) of your security programs.
FDJ, a Renowned Client Chooses Activity Monitoring
FDJ UNITED, a major European gaming operator, has implemented 5 pentest programs, 10 Bug Bounty programs, and 1 VDP program with Yogosha. This industry giant also relies on the Activity Monitoring feature, as confirmed by Jeremy Couture, CISO of FDJ United: “Monitoring—it really helps us understand if the security programs are on the right or wrong track.”
Like FDJ, take control of your asset security. Use Activity Monitoring to ensure complete test coverage and maximize your ROI.
Ready to find out how?