Uncover and manage critical vulnerabilities within days, not weeks
Agilely launch and manage your security tests from end to end with our vulnerability management platform and our Strike Force of 800+ cybersecurity experts.
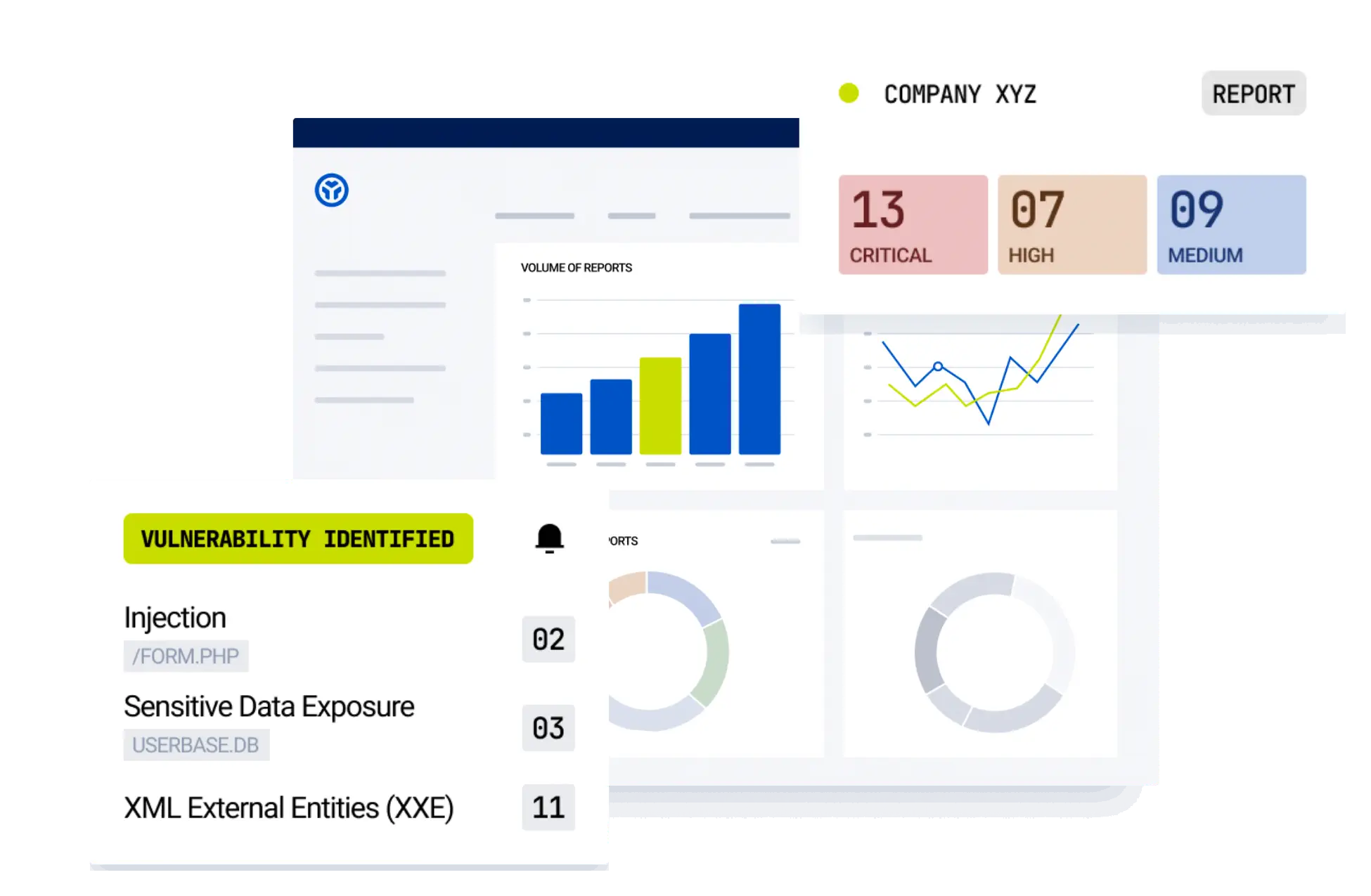











Offensive Security Operations
Tailored to your needs
Whether on-demand or continuous, Yogosha offers multiple security testing methods to match your security objectives and the maturity of your company’s assets.
Pentest as a Service (Ptaas)
Deploy a small team of skilled security researchers to audit and test your assets point in time and periodically. Your testing coverage is guaranteed and at a fixed cost.
- Access a vetted, skilled and international community of 800+ security researchers, specialized in different asset types
- Get critical vulnerability reports with proof of concepts, remediation guidance and direct communication with security experts

Bug Bounty
Deploy a large team of security researchers to test your assets continuously. You pay only when a valid vulnerability is submitted.
- Access a vetted, skilled and private community of 800+ security researchers, specialized in different asset types
- Pay only for valid vulnerabilities found
- Ensure continuous discovery of critical vulnerabilities with proof of concepts, remediation guidance and direct communication with security experts

Vulnerability Disclosure Program (VDP)
Ensure that anyone can securely submit a potential vulnerability to your organization following your instructions in a Vulnerability Disclosure Program (VDP).
Special Operations
Based on your needs, we offer ad hoc operations including Red Teaming, Threat Intelligence (TI), Hardware Pentesting, Social Engineering, Digital Forensics, and CTFs. Feel free to contact us if you have any special security testing needs.
The Yogosha Strike Force
800+ security researchers
Vetted and highly skilled
Only 10% of applicants are accepted into the Yogosha Strike Force (YSF). Our security researchers passed a technical and redactional test — which makes for clear and fully documented vulnerability reports. They’re also ID checked, and signed T&Cs with an NDA.
Seamless end-to-end vulnerability management
Uncover critical vulnerabilities you haven’t detected yet
Now your assets are safer
Made possible with our expert security researchers who are skilled in multiple asset types and hold certifications such as OSCP, OSEP and eWPTXv2.


Get real-time overview of your risk profile
Now you can keep control of your exposure
Made possible with our dashboard, featuring new reports sorted by criticality, triaged and rewarded reports, as well as retests.
Accelerate remediation
Now your developers can patch with confidence
Made possible with our fully documented vulnerability reports including CVSS score, proof of concept, remediation guidance and direct communication with security researchers.

Explore all of our platform features and benefits.
300+ Clients
12 Countries
6 Industries
”"With Yogosha, we have researchers who go really deep. Some of them place real orders on the website, so they spend their own money to find vulnerabilities. We’ve never seen that elsewhere."
Julien ReitzelLead Offensive Security — Veepee
”"We wanted to test hardware, and through Yogosha, we managed to find talented people. The security researchers found issues on all the equipment. The team was able to attack the hardware, but also the firmware. So we found vulnerabilities and areas of improvement on both dimensions."
Eric VautierCISO — Groupe ADP (Paris Airports)
”"For us, bug bounty was really complementary to other security tests and it brought its own added value. It allowed us to discover several vulnerabilities, which had not been seen before in the application."
David CrochemoreHead of the digital transformation team at the French Ministry of the Interior's Elections Department
”"I strongly urge all companies to implement bug bounty, all the more so if there’s any production involved. As soon as there’s a product development lifecycle, there has to be a bug bounty somewhere. And it doesn’t matter what policy and measures are already in place, whether there are in-house scanners and pentesting or not."
Zakaria RachidCISO — leboncoin
”"The simplicity of accessing the service is really appreciable, especially for small and medium-sized enterprises or start-ups. Launching a pentest can be complicated. You have to make contracts, which are sometimes hard to manage. Yogosha provides real flexibility."
Philippe Puyou LascassiesCISO — Terega
Featured Articles
Ready to secure your assets?
Uncover vulnerabilities, fortify your defenses, and stay one step ahead of cyber threats.




